COMPLAUD: monitoring information security, auditing standard compliance, tracking settings
Marketing materials
 Blog: COMPLAUD. Customer’s data security is our top priority!
Blog: COMPLAUD. Customer’s data security is our top priority!
Download a virtual machine with COMPLAUD agent installed
User documentation
COMPLAUD is:
 Real-time information on compliance and vulnerabilities in your entire infrastructure.
Real-time information on compliance and vulnerabilities in your entire infrastructure.
 Assurance of passing any audit of security standards.
Assurance of passing any audit of security standards.
 No dependency on the "human factor" in providing information security.
No dependency on the "human factor" in providing information security.
 A unified console for information technology management and information security.
A unified console for information technology management and information security.
 Continuous auditing of all installed software.
Continuous auditing of all installed software.
The problem of information security is a classic case of the "weakest link":
 You might have the most expensive firewall, yet it might be set to permit all access in all directions. In this case, you have a security tool, but it provides no security.
You might have the most expensive firewall, yet it might be set to permit all access in all directions. In this case, you have a security tool, but it provides no security.
 A key task for system administrators is bringing a broken system back up quickly. During the troubleshooting process, in order to ensure the systems work reliably within a short timeframe, the administrators will often disable certain security settings and assign excessive (or worse, maximum) permissions to themselves, other users, or system components. They will also install software and services that should not normally be running on servers. After resolving the problem, they often forget to bring something back to its original state. No malice is necessary, they are simply human.
A key task for system administrators is bringing a broken system back up quickly. During the troubleshooting process, in order to ensure the systems work reliably within a short timeframe, the administrators will often disable certain security settings and assign excessive (or worse, maximum) permissions to themselves, other users, or system components. They will also install software and services that should not normally be running on servers. After resolving the problem, they often forget to bring something back to its original state. No malice is necessary, they are simply human.
 New vulnerabilities are constantly being discovered in existing software. If a particular patch is not installed, even the safest previously configured system can turn into a "security hole".
New vulnerabilities are constantly being discovered in existing software. If a particular patch is not installed, even the safest previously configured system can turn into a "security hole".
Besides, software licensing is often flexible, permitting variations in the number of copies over time. From time to time, vendors conduct audits. Copies exceeding the currently licensed number can result in sizeable bills.
The typical response to these problems involves periodic manual audits. An audit like this is labor-intensive, so the usual frequency does not exceed once per quarter, or even per year. In the worst case, some of the hardware might never be audited at all.
Nobody can tell the exact state of things between audits.
The usual result of a manual audit is a text document or a set of work tickets. There is no verification that the detected vulnerabilities or violations are actually rectified. This can only be checked during the next planned audit.
Therefore, actual information security issues can lurk in your systems for a very long time without ever being detected or rectified.
As for the number of extra copies of installed software, administrators normally use manual control – which often realistically means no control at all.
What can the results be?
 Unauthorized access to information.
Unauthorized access to information.
 Leaks of data, including financial and personal data.
Leaks of data, including financial and personal data.
 Breakdowns in functionality of IT systems, which can mean breakdowns in the business.
Breakdowns in functionality of IT systems, which can mean breakdowns in the business.
 Loss of money and reputation due to all these problems.
Loss of money and reputation due to all these problems.
 Financial demands from software vendors.
Financial demands from software vendors.
What must be done to ensure real security (absence of known vulnerabilities and discrepancies) of IT systems and hardware at all times?
You must check everything constantly (for example, once every five minutes). If any security issues are detected, alerts must be sent both to those responsible for fixing the issues and those who can control those who resolve the issues. [or: “...and to those who must verify the fixes”]. If an administrator has disabled a firewall for troubleshooting and then forgot to re-enable it, all administrators and information security officers must know about it. When any new vulnerabilities were announced, administrators and security officers must know which particular IT systems and devices are vulnerable, so that they can commence rectifying them swiftly.
This process is implemented in COMPLAUD, a horizontally scalable information security and compliance audit system.
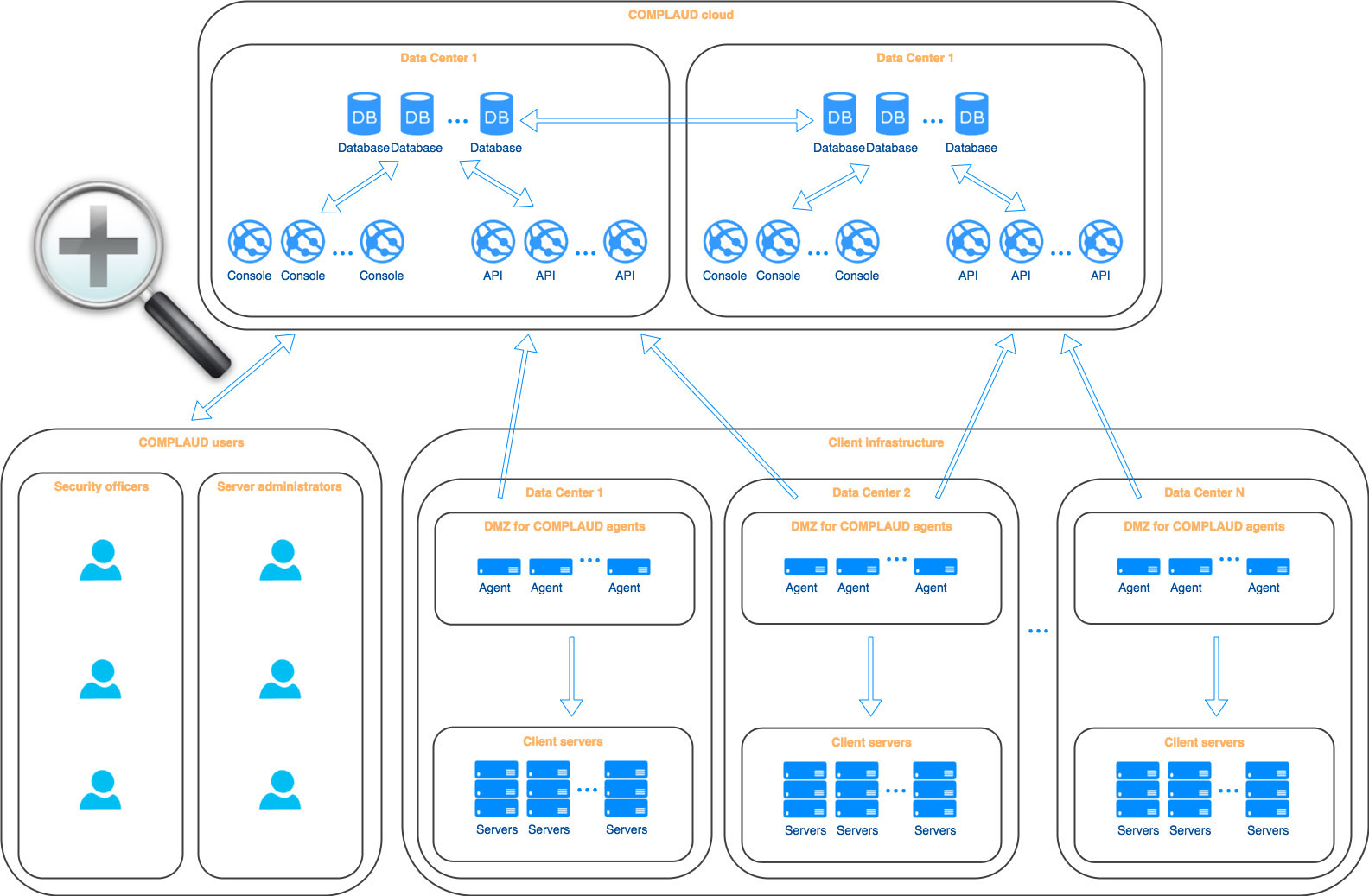
This system can easily handle monitoring security for any amount of infrastructure objects and IT systems. It checks for vulnerabilities according to its continuously updated database and for compliance with corporate security standards that you can configure. It can also audit the software that is installed on all the monitored objects. With COMPLAUD, you can view the actual picture of the state of security throughout your infrastructure and monitor the process of resolving any incompliance in practically real time.
COMPLAUD has a simple, convenient user interface and rich capabilities for integration with different monitoring and alerting systems.
COMPLAUD is available as a cloud service. It can also be deployed on the customer’s servers.
COMPLAUD is a control tool and also a tool that helps administrators in day-to-day information security tasks.
COMPLAUD provides technical assurance that IT systems, servers, and network devices are configured according to company standards and policies and are not affected by known vulnerabilities.
Some technical details of COMPLAUD
|
|
Horizontal scalability and resilience * |
|
A comprehensive and fully documented API enables automated interaction with the system interface |
|
|
Open source code for the agent and plugins ensures that the server audit process is transparent and customer-controlled |
|
Use of the HTTPS protocol for agent-to-API interaction enables further customization of client code for a particular client infrastructure |
|
|
Escalation of the generated events through syslog and into the Slack corporate messenger helps ensure prompt reaction from information system administrators when a vulnerability or incompliance is detected |
|
Integration with the Elasticsearch search engine enables storage and search of all the detected vulnerabilities and cases of incompliance, as well as logs of all user interaction with the system |
|
|
Web-based customization of compliance plugins enables flexible changes to the parameters that are monitored on every host |
|
Role-based access control helps organize interaction between security officers and information system administrators using Ticketing functionality |
* Technologies and solutions that enable horizontal scalability and resilience:
 Cassandra, a decentralized NoSQL DBMS, ensures linear scalability and replication between any number of cluster nodes located in several data centers
Cassandra, a decentralized NoSQL DBMS, ensures linear scalability and replication between any number of cluster nodes located in several data centers
 Round-robin DNS enables load balancing between identical API nodes that process data sent from agents
Round-robin DNS enables load balancing between identical API nodes that process data sent from agents
 Nginx, an asynchronous Web server, processes agent requests to the API. The amount and rate of requests can rise with practically no limits
Nginx, an asynchronous Web server, processes agent requests to the API. The amount and rate of requests can rise with practically no limits
Functional features
 Vulnerability (Audit) based on over 14 thousand vendor security publications (Red Hat Enterprise Linux, CentOS, Ubuntu, Suse Linux Enterprise Server)
Vulnerability (Audit) based on over 14 thousand vendor security publications (Red Hat Enterprise Linux, CentOS, Ubuntu, Suse Linux Enterprise Server)
 Security configuration (Compliance) checking for Linux and MS Windows devices
Security configuration (Compliance) checking for Linux and MS Windows devices
 Software inventory
Software inventory
Security
 Users and agents interact with the system using the encrypted HTTPS protocol
Users and agents interact with the system using the encrypted HTTPS protocol
 Confidential user data stored in the system is encrypted using the AES algorithm with a 256-bit key
Confidential user data stored in the system is encrypted using the AES algorithm with a 256-bit key
 MS Active Directory integration using the LDAP protocol ensures an approach to authentication and authorization procedures that is standard for corporate environments
MS Active Directory integration using the LDAP protocol ensures an approach to authentication and authorization procedures that is standard for corporate environments
Architecture diagram for the cloud version
To evaluate COMPLAUD for your company, contact info@rcntec.com or call the numbers
8 (800) 302 87 87 (for calls from Russia) and +7 (495) 009 87 87 .